The holiday season is upon us and many of us are planning our travels. This season, be prepared to add some new items in your dos and don’ts. A vastly unknown threat to our mobile devices is “Juice Jacking”.
When your smartphone battery runs out and you're stuck somewhere, you might not hesitate to plug in at the nearby USB charging station.
Wait a minute. Juice jacking warnings can make you rethink your decision.
One of these public charging stations may have had malware installed on the USB port or the USB cord. A virus or other malware that can follow your keystrokes or even steal your data might be installed on your phone while it is charging.
Although juice jacking does not yet seem to be a common issue, it is still a good idea to be aware of your risks and available options before charging your battery at a public charging station, such as one found at an airport.
Smartphones all have the same feature: The power supply and data stream travel over the same wire, whether you have an iPhone, BlackBerry, or Android handset.
This might be problematic. Your phone establishes a trusted connection with the device it connects to by pairing with it. That implies that the gadgets can exchange data. Consequently, a cybercriminal may be able to access your device over the USB cord while it is being charged.
The connection is only visible on the end that supplies power, and on most phones the data transfer is deactivated by default (except from older Android smartphones).
For instance, a message on the computer may ask you whether to trust the device when you link your phone into it. Juice jacking prevents the device owner from seeing what the USB port is connected to. Therefore, if someone is checking on the other end when you connect in the phone, they might be able to transfer data from your device to theirs.
Data Theft: When a device is plugged into the public USB port, a cybercriminal could have compromised that port and enabled malware to infect your plugged-in device. This could potentially allow someone to steal the data on your mobile device.
Using a crawler program on your device, a cybercriminal could then search for personally identifiable information, account credentials, and financial information.
If the perpetrator can transfer that data onto their device, it might be enough personal information to impersonate you or access your financial accounts.
Malware Installation: Cybercriminals may use a malware app to clone your phone data and transfer it back to their own device. Other malware may help them gather data such as your GPS location, purchases, social media interactions, photos, and call logs.
Some types of malwares include adware, crypto miners, spyware, Trojans, or ransomware. Once your device is frozen or encrypted with one of these types of malware, the cyber-thief may demand payment to restore the information.

Avoid public charging stations or portable wall chargers:
Think ahead. Get into the practise of charging your phone when it's not in use at home, at work, or in the car.
If you must charge your phone, use a wall outlet:
At a standard AC wall plug, data cannot be transferred between your devices. Therefore, think about using a wall socket if you urgently need to charge while out in public. Additionally, if you're travelling, be sure you have the right adaptor before you go.
Use software security measures:
Always lock your phone to prevent pairing with other connected devices. The phone can also be turned off before charging, but the USB port might still be able to communicate with the device's flash storage. You can completely disable pairing if your iOS device has been jailbroken.
Choose a different method to charge your phone:
You have the choice of using external batteries, wireless charging devices, or power banks, which you can charge at home and take with you wherever you go. Most power banks are portable, flat, and lightweight.
Use USB pass-through devices:
These adapters allow power to flow through but disable the data pin on the USB charger. That means the device charges, but data won't transfer.
MFA Self Help Guide
We have introduced Multifactor Authentication in our organization to add an extra layer of security. This extra layer safeguards your valuable credentials from being misused. MFA is a combination of 2 or more factors. Let’s see what those factors are:
· Something that you know (Password)
· Something that you have (Unique code)
· Something that you are (Biometrics)
Having only one factor in place creates a single point of failure which can have serious security breach incidents. Hence, we have started rolling out MFA for our dear users in order to protect them from bad actors. This article has an attached self help guide for the MFA setup.
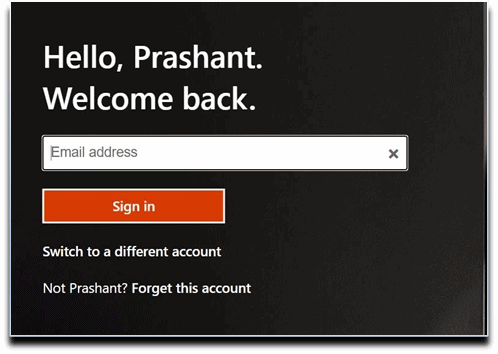
2. Select Use my password.

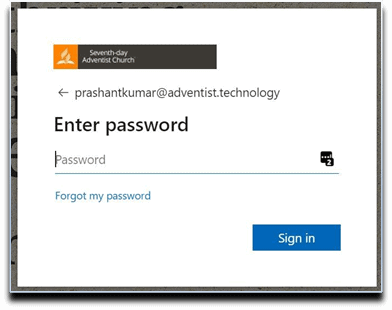
3. Specify network password. Select Sign In
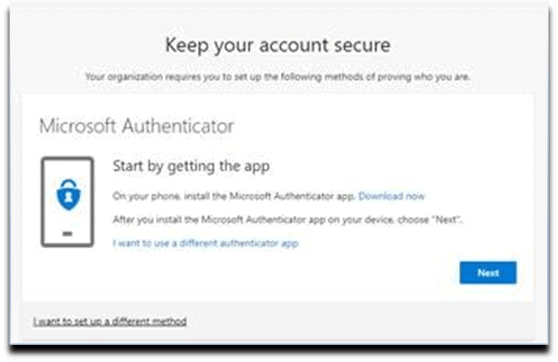
4. Procuring the Microsoft Authenticator App. Selected Download Now link
5. Microsoft Authenticator Download Screen – targeted.
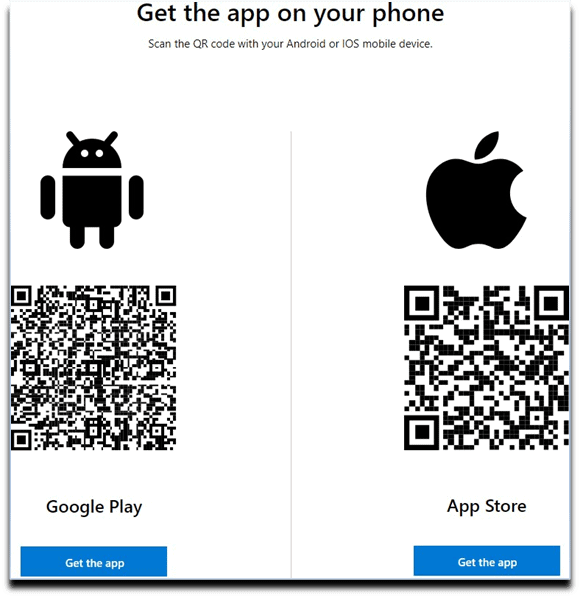
6. Scan the code as per your device type.
7. Return to Screen 4. Select Next.
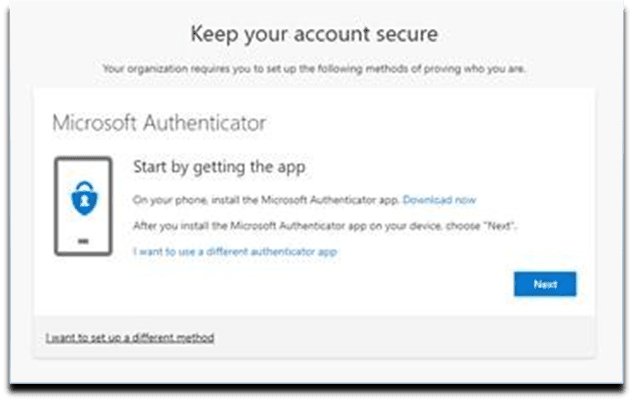
8. Select Next button.
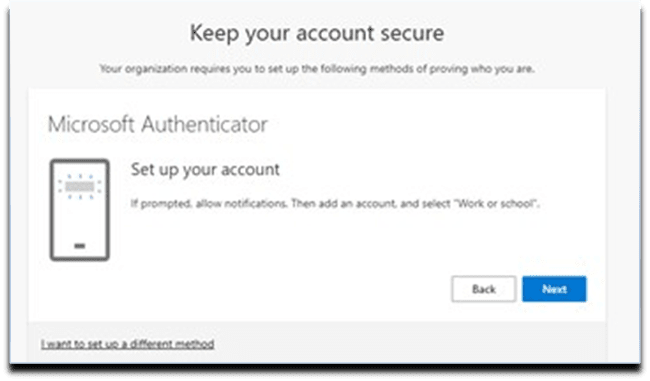
9. Scan QR code from within Microsoft Authenticator App. Select Next button.
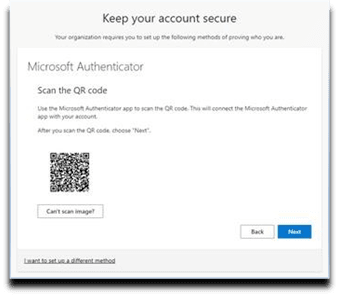
10. Select the account as Work/School.
11. Approve Notification in Authenticator App.
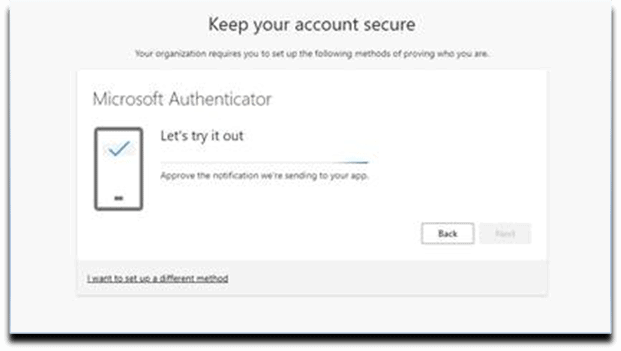
12. Mobile Device. Approve Notification in App.
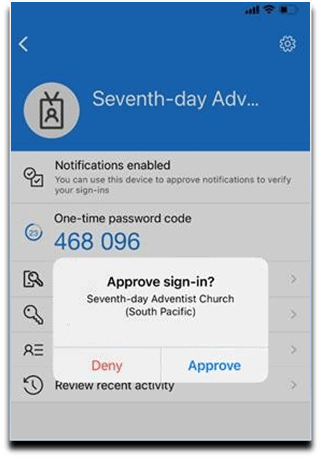
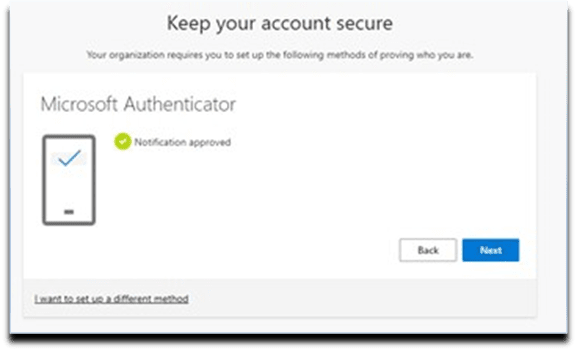
13. Setup. Notification Approved. Select Next button.
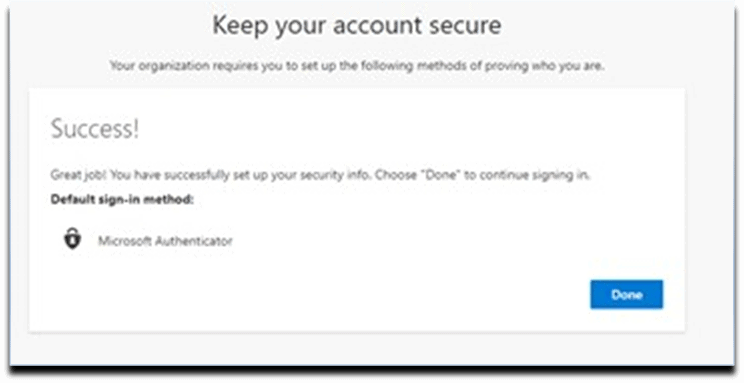
14. Setup. Success Screen. Select Done button.
Sure you recognise the name, but are you sure that email asking you to download or visit a site is from your work colleague?
We have noticed a steady increase in malicious emails that are crafted to look like they are from trusted internal email addresses along with more examples of complex phishing scenarios targeting individuals in our offices. We are doing our best in the background to help catch these emails however some unfortunately do slip through.
As an added defense we need your help so we are adding a new banner to all inbound emails that originate from an external source. It will serve two purposes:
Internal emails will have NO banner. That does not mean they are guaranteed to be safe. As peoples’ mailboxes can be compromised too but is less likely if we all keep our passwords complex, secure and unique per site. Regardless if something doesn’t feel right, seek clarification via the phone.
External email will have an added banner that looks like this;

This is something you will notice many other companies doing now and is considered “best practice” and is just one tool in the toolbox to try and keep our emails safe. We know it may not look aesthetic, but its function is to raise awareness. Thank you for being accommodating and working with us as we seek to improve our email security in this ever-changing landscape of internet security.
Millions of email addresses and associated passwords are compromised every day on the web. Data breaches are making it increasingly less secure to rely only on using passwords, so what measures can you take to improve your online security and protect your identity?
TWO-FACTOR authentication (2FA or MFA) requires a user to provide two different types of information to gain access to an online account or computer system. A factor in this context is a way to prove that “you are who you say you are”, so the system knows you are legitimate and authorised to access the service. By far the most common authentication factor in use today is a username and password. This is known as a single factor. It is one factor of identification, a password. With 2FA, you need to provide a password and prove your identity in some other way to gain access. As passwords have become increasingly less secure, it is increasingly important to enable 2FA on any accounts to add that extra layer of security.
Millions of email addresses and associated passwords are available on the dark web because of major data breaches which make only using passwords increasingly less secure. Also, as most people use the same password across multiple sites and accounts, a hacker can gain access to users’ other accounts by using robots to trawl the internet with known email addresses/passwords and thus gaining access to users’ data easily and most times the users will not be aware malicious actors have gained access. Something also to be mindful of is that many sites use security questions or knowledge-based authentication—"What's your pets’ name?" or "What city were you born?"—as a backup to passwords. Unfortunately, so much personal information is publicly available now through social media and data breaches that a determined hacker can find these answers and compromise an account. More importantly, those questions aren't a true second factor and therefore don't provide the layered security of 2FA.
Think of a factor in abstract terms: It’s something you know or have. That’s why using security questions isn’t the same as having real 2FA; you're just backing up something you know with something else you know. True 2FA pairs the first authentication factor, something you know—usually a password—with one of the other two factors, which are entirely different: Something you have might be a code texted to your mobile, or an app on your phone that displays a temporary code, for example, a fingerprint.
Figuring out how to enable two-factor authentication for all your accounts can be daunting. Apple, Microsoft, Google, all the major social media sites, Amazon, popular services like Slack and Dropbox all offer 2FA. A quick web search should lead you to instructions on how to enable 2FA on your accounts. And you can always ask our friendly team at Adventist Technology Service Desk for advice. Taking the extra step for security now can save you a lot of headaches in the future. Adventist Technology now has a dedicated team focusing on keeping our organisations safe digitally. Working hard behind the scenes to develop a comprehensive set of policies that can be used by any Adventist entity. If you are interested let us know we are happy to share them with you. We also review all our information-based assets and working to develop good governance to help manage these securely. Over the coming months, we will share insights and guidelines to help you navigate the challenges of cyber security. One of the most important things you can do today is to enable multi-factor authentication on your accounts. As pointed out in this article 2FA is one small step that has a significant improvement in securing our accounts and is now considered best practice.